
How-to
Empowering engineers with everything they need to build, monitor, and scale real-time data pipelines with confidence.
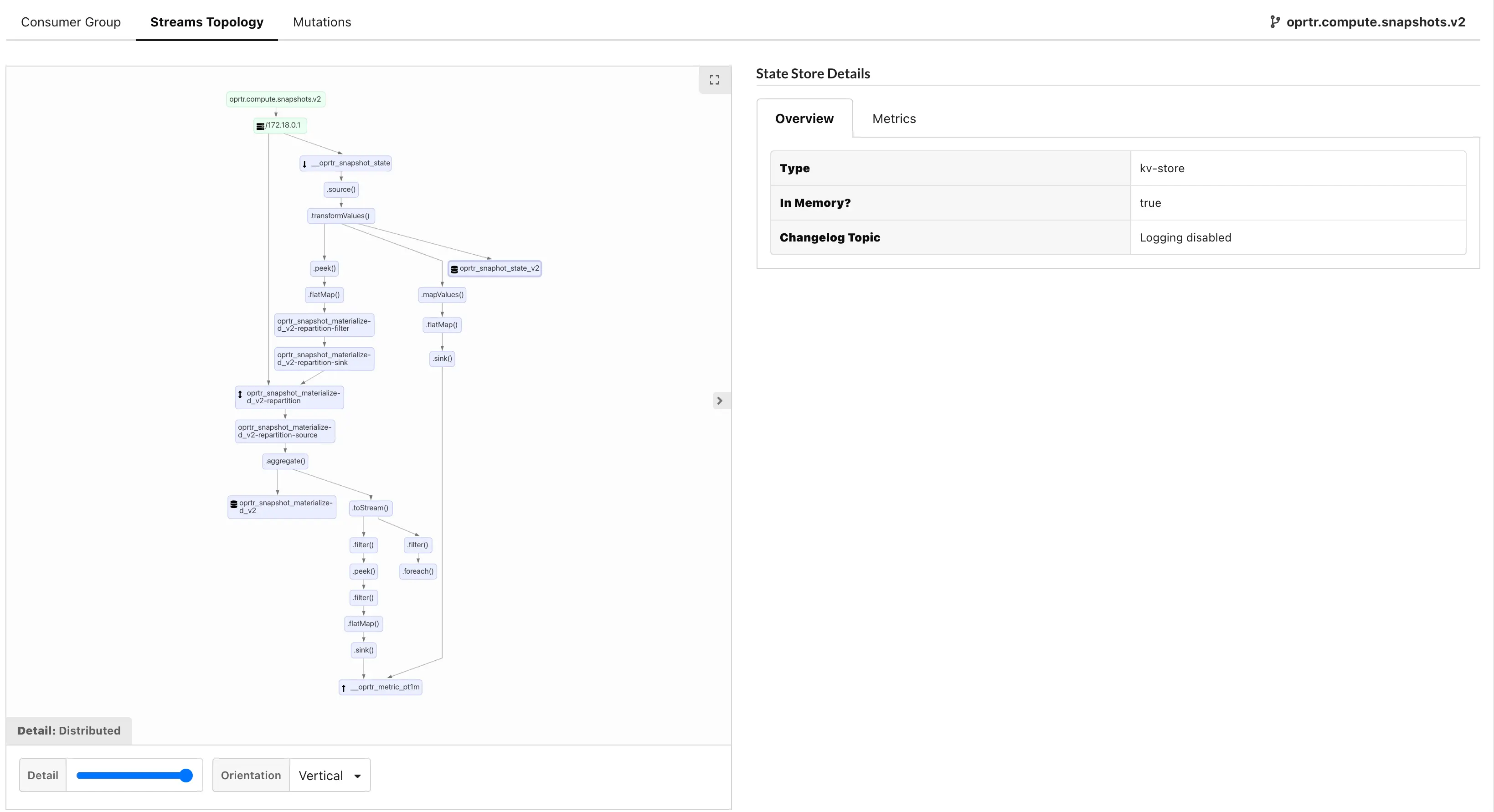
Deploy Clojure Projects to Maven Central with Leiningen
This article provides a step-by-step guide to how we deploy the Kpow Kafka Streams Monitoring Agent to Maven Central with Leiningen.

Run Kpow in Kubernetes with Helm
This article covers running Kpow in Kubernetes using the Kpow Helm Chart. Introduction Kpow is the all-in-one toolkit to manage, monitor, and learn about your Kafka resources. Helm is the package manager for Kubernetes. Helm deploys charts, which you can think of as a packaged application. We publish...

Kafka Alerting with Kpow, Prometheus and Alertmanager
This article covers setting up alerting with Kpow using Prometheus and Alertmanager. Introduction Kpow was built from our own need to monitor Kafka clusters and related resources (eg, Streams, Connect and Schema Registries). Through Kpow's user interface we can detect and even predict potential problems...
Join the Factor Community
We’re building more than products, we’re building a community. Whether you're getting started or pushing the limits of what's possible with Kafka and Flink, we invite you to connect, share, and learn with others.


