Rapid Kafka Diagnostics: A Unified Workflow for Root Cause Analysis
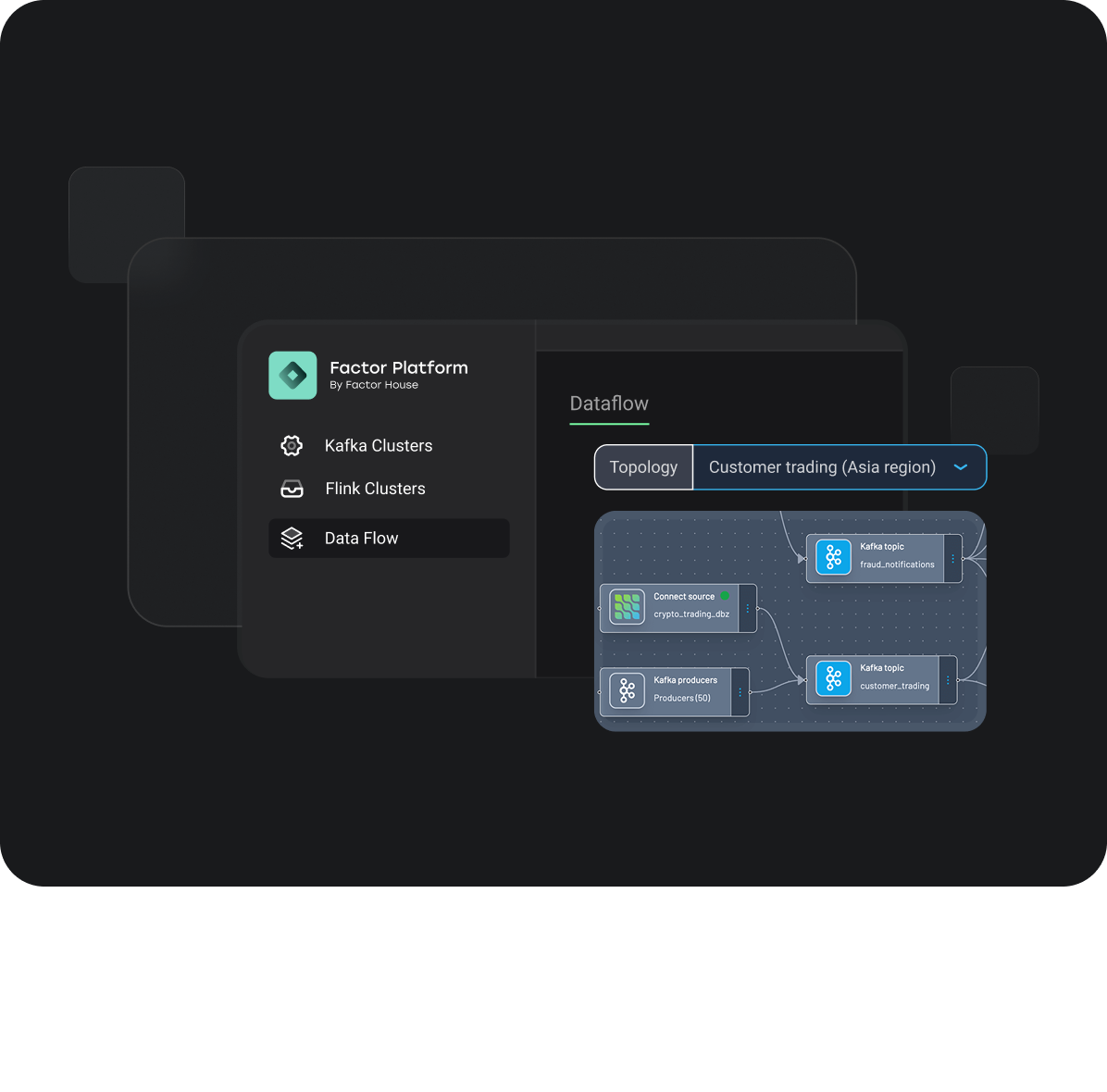
The Context Gap caused by fragmented tools hinders effective Kafka monitoring and troubleshooting, as it forces engineers to manually piece together logs and metrics. This guide demonstrates how to close that gap using Kpow's unified workflow to identify the stall, inspect the data, and resolve the incident in a single interface.


.png)
.png)
.png)

.png)

.png)


%201.png)

.png)
.png)
.png)

.png)

.png)

.png)

.png)



.png)
.png)
.png)
.png)
.png)

.png)

.png)
.png)
.png)

.png)

.png)

.png)


%20(1).png)
%20(1).png)
.png)






















.png)

