
Release 89.4: Connect Inspect RBAC Permission

Release Info
Kpow can be found on Dockerhub
docker pull operatr/kpow:89.4View our Docker quick start guide for help getting started.
Kpow can be found on ArtifactHub
Helm version: 1.0.39
helm repo add kpow https://charts.kpow.io
helm repo update
helm install --namespace factorhouse --create-namespace my-kpow kpow/kpow --version 1.0.39 \
--set env.LICENSE_ID="00000000-0000-0000-0000-000000000001" \
--set env.LICENSE_CODE="KPOW_CREDIT" \
--set env.LICENSEE="Your Corp\, Inc." \
--set env.LICENSE_EXPIRY="2024-01-01" \
--set env.LICENSE_SIGNATURE="638......A51" \
--set env.BOOTSTRAP="127.0.0.1:9092\,127.0.0.1:9093\,127.0.0.1:9094" \
--set env.SECURITY_PROTOCOL="SASL_PLAINTEXT" \
--set env.SASL_MECHANISM="PLAIN" \
--set env.SASL_JAAS_CONFIG="org.apache.kafka.common.security.plain.PlainLoginModule required username=\"user\" password=\"secret\";"
--set env.LICENSE_CREDITS="7"View our Helm instructions for help getting started.
Kpow can be found on the AWS Marketplace
View our AWS Marketplace documentation for help getting started.
Kpow can be downloaded and installed as a Java JAR file. This JAR is compatible with Java versions 11+.
View our JAR quick start guide for help getting started.
Kpow can be downloaded and installed as a Java JAR file. This JAR is compatible with Java 8.
View our JAR quick start guide for help getting started.
For more information, read the Kpow accessibility documentation.
Kpow v98.4 introduces a new CONNECT_INSPECT RBAC permission and fixes a number of minor UI bugs.
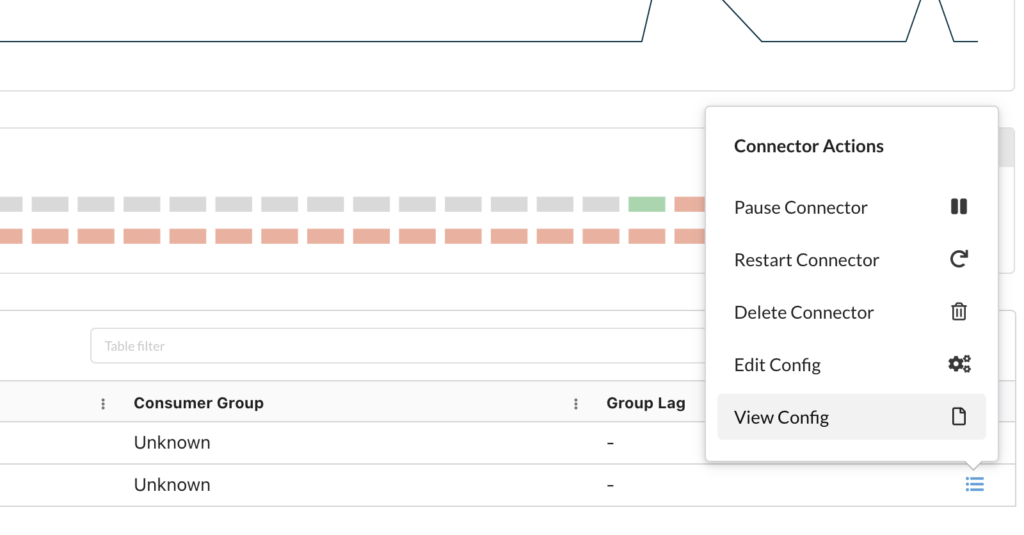
CONNECT_INSPECT
A new 'View Config' action allows users to view connector configuration without entering the full connector edit UI.
This action is guarded by a new RBAC permission, CONNECT_INSPECT.
Provide users this permission and deny CONNECT_EDIT to allow users to view connector configuration without allowing them to edit connectors.
Users who have CONNECT_EDIT are considered to automatically also have CONNECT_INSPECT (editing a connector means you can see its configuration).
Set ALLOW_CONNECT_INSPECT to apply this new permission when using global access controls, or add CONNECT_INSPECT to your existing RBAC configuration as you would any other permission.
Release v89.4 Changelog
See the Factor House Product Roadmap to understand current delivery priorities.
Kpow v89.4 Changelog
See the full Kpow Changelog for information on previous releases
- Improve connect RBAC with CONNECT_INSPECT permission
- Improve connect error messaging
- Fix schema subject delete bug
- Fix staged mutations table bug

Release 95.3: Memory leak fix for in-memory compute users
95.3 fixes a memory leak in our in-memory compute implementation, reported by our customers.

Release 95.2: quality-of-life improvements across Kpow, Flex & Helm deployments
95.2 focuses on refinement and operability, with improvements across the UI, consumer group workflows, and deployment configuration. Alongside bug fixes and usability improvements, this release adds new Helm options for configuring the API and controlling service account credential automounting.

Release 95.1: A unified experience across product, web, docs and licensing
95.1 delivers a cohesive experience across Factor House products, licensing, and brand. This release introduces our new license portal, refreshed company-wide branding, a unified Community License for Kpow and Flex, and a series of performance, accessibility, and schema-related improvements.
Start your streaming transformation today.
Try both Kpow or Flex free for 30 days with a single license - no credit card required.
